SEL-735 Remote Access
During a recent engagement with a large Green Energy client I noticed a large amount of Telnet ports open on their IPs.
Further investigation of this found to be preporting from SEL-735 devices show below:
Grabbing the banner for this telnet service, I thought to run it through Shodan and see what was out there:
Amazingly I could see thousands of these SEL-735 devices, which appear to be commonly used to clean the quality of power coming out of solar arrays as well as compute financial earnings for the user.
Diving a little deeper I can see that these devices are supposed to be administrated locally using SEL’s propriatary software AcSELerator:
But it appeared to actually be using Telnet under the hood to communicate.
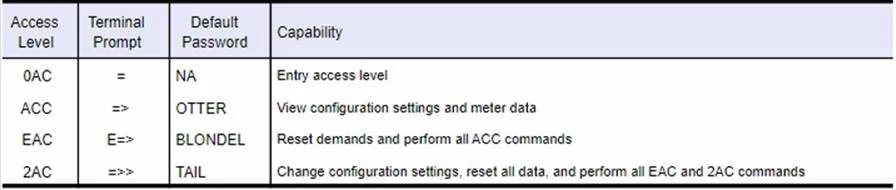
The obvious next step would be to google to see if these devices have any form of default creds. And wouldn’t you know it, right there in the free to download manual:
So I tried it on one of my clients devices and it let me straight in!
Realising there is a fairly easy 2000+ device botnet-to-be on the internet, I reached out to SEL to report this, who stated that the device is operating as expected and that they strongly suggest not connecting to these devices over the internet. So while they don’t appear to plan on changing this, they did however give us permission to publish this!
So as the old Red Team saying goes: IoT very much stands for Infrastructure on Tap.